What’s Happened?
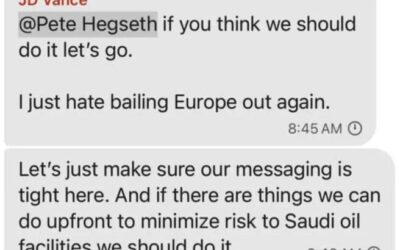
The hacker has been hacked. Or, at least, a lot of their documents have been leaked.
And it turns out that Pegasus, the name for the family of spyware tools developed by NGO Group, an Israeli cyberweapons firm, has been sold to authoritarian regimes around the world to spy on dissidents, journalists, human rights activists, lawyers and many others.
There’s so much to this story and so much to be concerned about it’s hard to know where to start. So start here.
What is Pegasus Spyware?
Pegasus spyware is capable of infecting billions of phones running either iOS or Android operating systems.
Some versions of Pegasus use phishing emails to trick a target into clicking a malicious link. Other versions don’t require any action by the user, taking advantage of vulnerabilities in a phone’s operating system. In the past WhatsApp calls and Apple iMessages have been used to attack phones.
What Information Can Pegasus Exfiltrate?
Once Pegasus has infected a phone, it can extract almost any information or file. SMS messages, contacts, call history, calendars, emails and internet browsing histories can all be exfiltrated to the attacker.
Who Are the Attackers?
We don’t have a full list but NGO Group’s customers appear to include the governments of Mexico, Morocco and the United Arab Emirates.
Who Has Been Attacked?
We have a list of over 50,000 phone numbers that were being spied on by NSO Group’s software. They include business executives, religious leaders, academics, NGO employees, government officials, journalists, lawyers, cabinet ministers, presidents and prime ministers.
Have I Been Attacked?
If you or someone in your company knows how to use the command line, you can check if your phone has been hacked using this tool.
How Can I Protect My Workers?
As Claudio Guarnieri, who runs Amnesty International’s Security Lab says, where attackers exploit “zero day” vulnerabilities, “the real honest answer is nothing”.
Of course, that is a frightening thought. But the reality is that the vast majority of cybersecurity attacks can be prevented through the adoption of best practices around things like data protection, email, passwords, firewalls, security systems, updates and staff training.