A TEAM FROM WORLD CLASS INSTITUTIONS





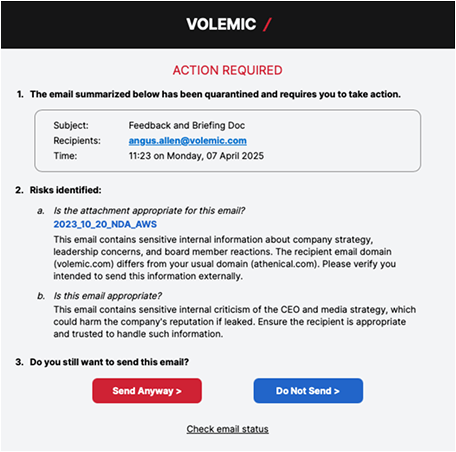
OVERVIEW
Email intelligence for cloud email.
Volemic stops the emails people wish they could take back — while making them feel supported, not scrutinized.
Stop
Mistakes
Stop
Misconduct
Stop
Manipulation
Mistakes Engine
- ✓Stop misdirected emails and incorrect attachments.
- ✓Stop autofill mistakes, reply-all errors and failure to use Bcc.
- ✓Stop sharing of excessive levels of PII and PHI.
Misconduct Engine
- ✓Stop malicious or negligent data exfiltration.
- ✓Stop policy breaches.
- ✓Stop regulatory violations.
- ✓Stop legal violations.
Manipulation Engine
- ✓Stop engagement with spear-phishing emails and social engineering attacks.
- ✓Alert users engaging with suspicious senders and new domains.
94% of cyber-threats originate in email.
2019 Data Breach Investigations Report
Verizon
94%
Percentage of cyber-threats originating in email
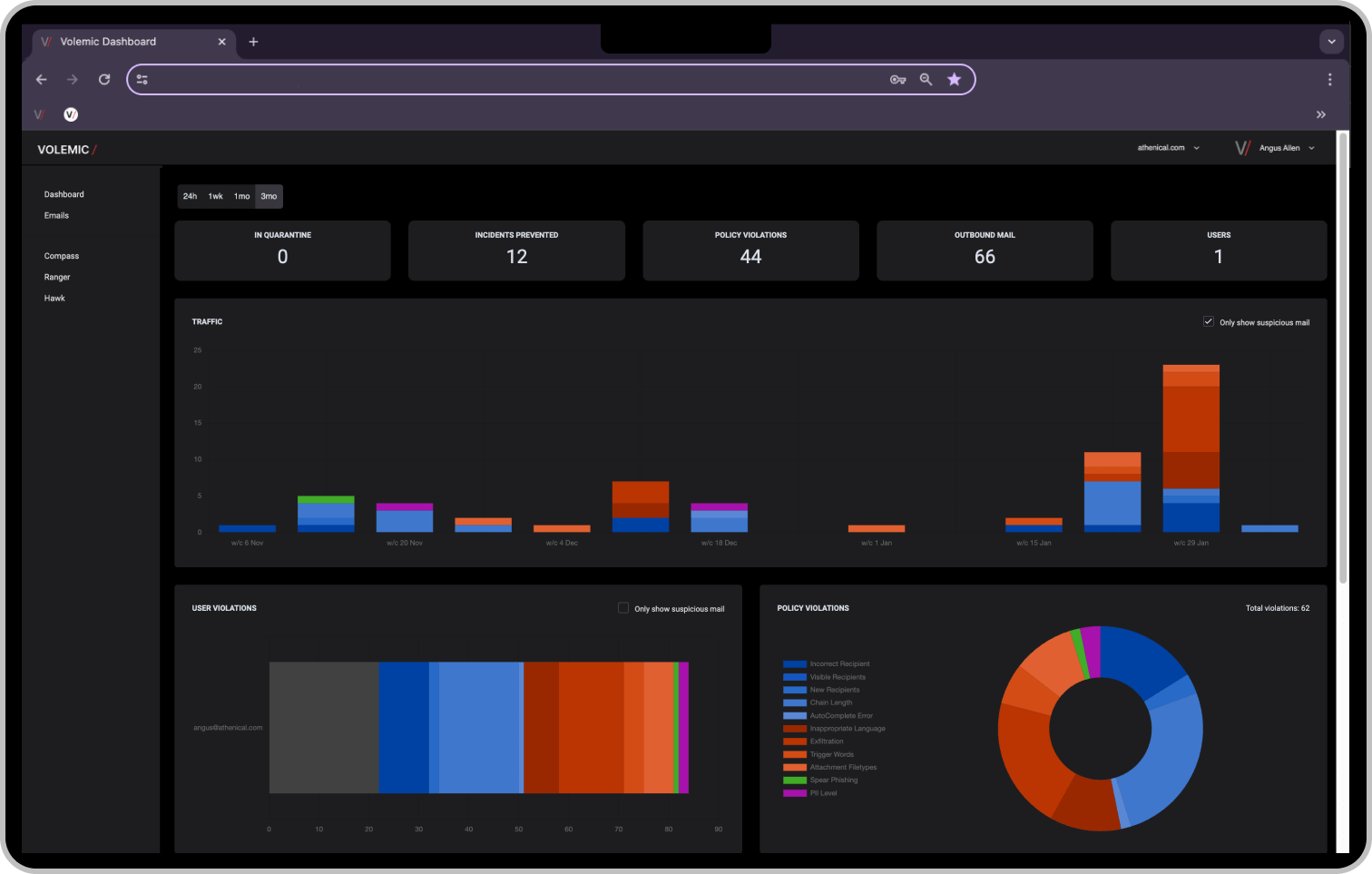
HOW IT WORKS
The 3-steps to advanced protection.
Volemic’s superhuman understanding of human behavior and language prevents human risks in email conversations and delivers AI decision support and training to at risk staff.
STEP ONE
Understand the human layer.
Volemic analyzes how your people naturally communicate — learning behavior, language, and patterns to define what’s normal for each individual and team.
STEP TWO
Stop risks in real-time.
Volemic’s intelligent AI learning system scans every email sent by employees and other insiders in real-time, looking for abnormal and risky emails or attachments, intercepting policy breaches before they leave the organization.
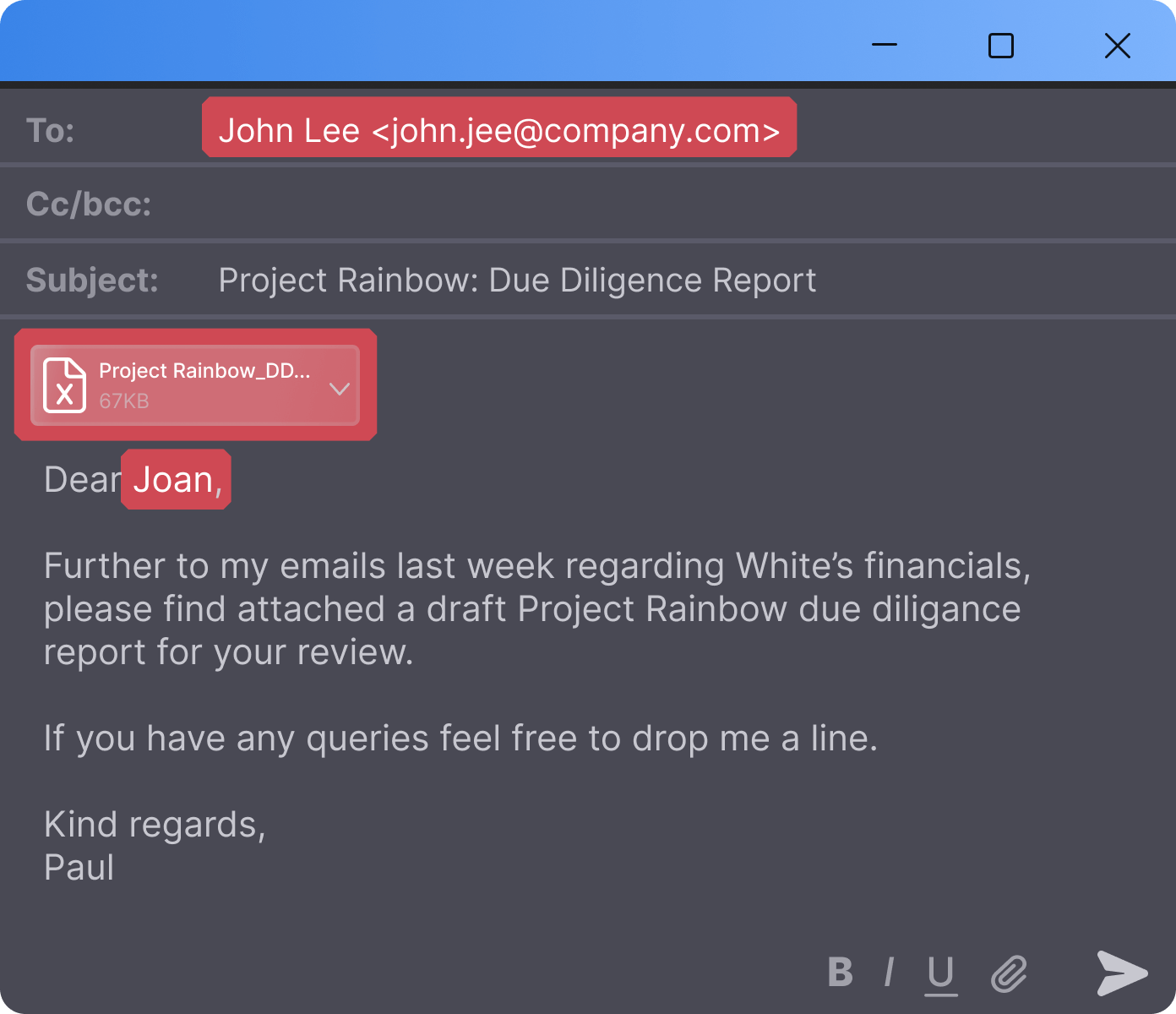

STEP TWO
Stop risks in real-time.
Volemic scans every email in real time — detecting risky messages or attachments and stopping policy breaches before they leave your organization.
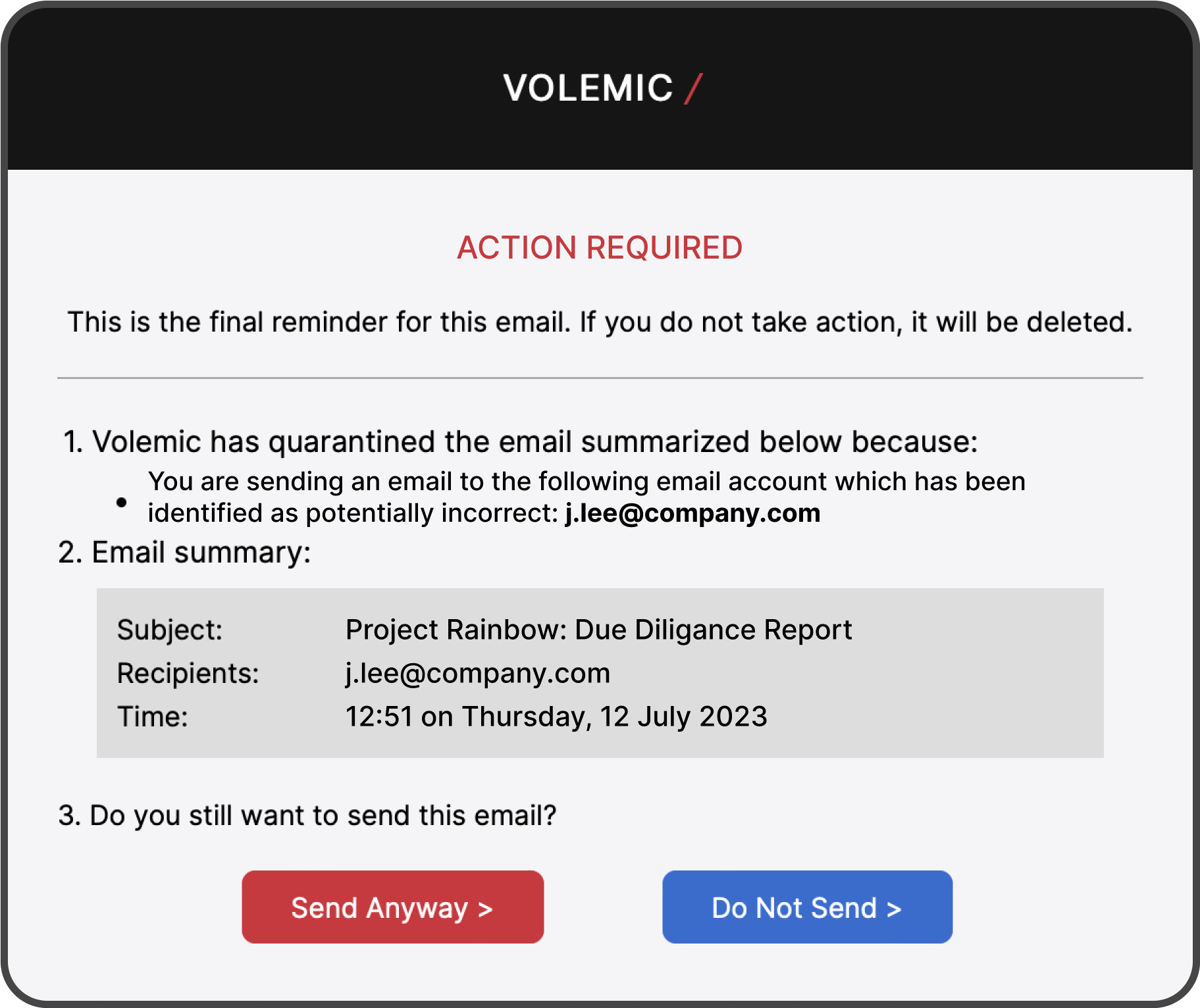
STEP THREE
AI decision support.
When a risk is intercepted, Volemic alerts the user with real-time, context-aware feedback — empowering them to make the right call before anything leaves the organization.
Data emailed to the incorrect recipient is the single biggest cause of reported data breaches, occurring 35% more frequently than all phishing, ransomware and malware attacks combined.
Data Security Incident Trends, 2024
Information Commissioner’s Office, UK
135%
Data breaches from misdirected emails compared to phishing, ransomware and malware combined
See Volemic in action.
Learn how Volemic can help you prevent human risk in email conversations with a platform loved by humans, so you can do more and worry less.
ELIMINATE HUMAN RISK IN EMAIL CONVERSATIONS
Intercept risk. Empower better decisions. Protect every email conversation.
Volemic scans every email in real time to prevent misdirected messages, policy breaches, and sensitive data loss — before they happen. Seamless to deploy, it integrates with Microsoft 365 in under an hour and empowers employees with smart, in-the-moment guidance that reduces risk without adding security team overhead.
INTERCEPT ADVANCED THREATS
Stop novel and evolving risks — without disrupting employees.
Volemic’s intelligent AI continuously adapts — learning from behavior, new information inside your organization, and external threat intelligence — so your people stay protected from emerging risks, automatically and invisibly.
EMPOWER BETTER DECISIONS
Deliver real-time, personalized coaching that changes behavior.
Volemic sends in-the-moment guidance tailored to each user’s behavior and risk profile — helping them make smarter, safer decisions. Reinforce the importance of security and compliance without adding overhead or friction.
MINIMIZE DISRUPTION
Move beyond “computer says no”.
Training can’t eliminate human error — and blunt controls frustrate your people and slow down business. Volemic stops only truly risky emails, so your team can work efficiently without unnecessary interruptions.
UNIVERSAL COVERAGE
Protect everyone, everywhere.
In a world of remote and hybrid work, Volemic ensures your people are protected — whether they’re working from a work or home device, in the office or on the move.
NO OVERHEAD FOR SECURITY TEAMS
Fully automated, no supervision required.
Security and compliance teams are under more pressure than ever — with less time and tighter budgets. Volemic’s Email Intelligence Platform eliminates the need for constant oversight, integrates seamlessly with your existing tech stack, and takes less than an hour to deploy.
Following a number of regulatory breaches caused by misdirected emails, we agreed with our regulator and our clients to implement a technical solution, and have not looked back since speaking to Volemic.
General Counsel, H2 2024
Leading international law firm with offices across 21 locations
BUILT AROUND YOUR RISKS
You describe it, we stop it.
From misdirected emails, data loss and engagement with AI-powered social engineering attacks, to policy, regulatory and legal violations — Volemic lets you define the risks that matter most to your organization. Our AI understands behavior, language, and intent, so it can prevent those risks in real time, without rules or manual oversight.
AWS PERFORMANCE AND RESILIENCE
Hosted securely on AWS. Seamless integration with your mail service.
Running on-premises email infrastructure is costly, complex, and hard to scale securely. Volemic’s AWS solution delivers resilience, performance, and dynamic threat detection — so your team can stay focused on the business, not the backend.
The only action type that is consistently increasing year-to-year in frequency is Error. That isn’t really a comforting thought, is it? Nevertheless, there is no getting away from the fact that people can, and frequently do, make mistakes and many of them probably work for you.
2020 Data Breach Investigations Report
Verizon
ENTERPRISE-GRADE SECURITY
World-class protection you can trust.
Hosted securely on AWS and built using configuration best practices, Volemic protects your data with bank-level 256-bit encryption at rest and in transit. Our platform is independently pen-tested, monitored 24/7, and designed with fault-tolerant infrastructure and full disaster recovery — so you can stay secure, compliant, and operational at all times.
AUDIT TRAIL
Minimize compliance risk.
Running on-premises email infrastructure is costly, complex, and hard to scale securely. Volemic’s AWS solution delivers resilience, performance, and dynamic threat detection — so your team can stay focused on the business, not the backend.
PROTECT YOUR BOTTOM LINE
Human risk in email converations is surging.
In the Conversation Economy, most high-stakes interactions now happen over email — and the cost of mistakes is rising fast. The UK’s ICO reports that sending data to the wrong recipient is the #1 cause of security incidents. IBM puts the average cost of a phishing breach at $4.5 million. And Ponemon estimates it takes 72 hours to detect and resolve a data loss incident.
Ignoring the human components, and thus neglecting usability issues, is one of the largest causes of security failure.
Security Engineering — 3rd edition
Ross Anderson, Professor of Security Engineering, University of Cambridge
See Volemic in action.
Learn how Volemic can help you prevent human risk in email conversations with a platform loved by humans, so you can do more and worry less.